(formerly supported by Microsoft Research Asia)
SecHCI is a knowledge-based identification system. In SecHCI, the secret knowledge shared between you (prover) and the computer (verifier) is not yet textual password like "intel123", it is a set of K secret objects (pass-objects). Here, "objects" can be characters, words, names of your friends, and pictures (icons, cartoon figures, human faces, and even Chinese characters). In our demonstration system, 1405 different icons randomly collected from Internet are used as candidate objects.
To prove yourself to the SecHCI system, what you should do is just to enumerate how many pass-pictures occur in MT challenges, where each challenge contains L pictures. Assume the number of pass-pictures in one challenge is S then you should tell the SecHCI system S mod 4 is "0/1" or "2/3" as a binary response. As an example, see the following table for one challenge and its right response:
| Password: |
|
| Challenge: |
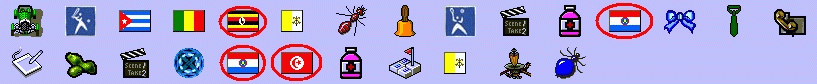 |
| Response: |
S=4, then S mod 4=0, so you should
select "0/1"
|
Apparently, for MT challenges, the probability of successful guess is 2-MT. If SecHCI is used in ATM machine of banks to withdraw money, MT>=20 is enough for 6-digit banking cards and MT>=14 is enough for 4-digit banking cards. Initial tests have shown that users can identify themselves within 5 minutes when MT=20, and can do so much more quickly if they have made such responses for many times (less than 2 minutes may be possible).
In each challenge, how should SecHCI generate decoy pictures (i.e., the ones that are not your pass-pictures)? If we randomly select decoy pictures from all available pictures, an attacker can find which pictures are pass-pictures by intersection of pictures in all challenge. This problem has also been mentioned in Deja Vu system (however, no essentially effective solutions have been suggested) [4]. In SecHCI, a practical solution is used as follows: users also select N' decoy pictures from all available pictures. All challenge-pictures are only generated from the current user's K pass-pictures and N' decoy pictures.
Furthermore, if the occurrence probability of each decoy-picture is different from the probability of each pass-picture, it will be still possible for an attacker to find pass-pictures by observing the occurrence of all pictures in challenges. That is to say, balance property should be satisfied for SecHCI. To do so, the following relation should hold: KL=3N, where N=N'+K. In addition, the generation of each challenge should yield some other rules, which will be analyzed in our submission to USENIX Security Symposium 2003.
Notice: Please note that you SecHCI CANNOT provide any security against peeping attacks, if you are eavesdropped when you set or change your password and/or decoy-pictures. You SHOULD only set and change your password and/or decoy-pictures when you can ensure the security of the setting procedure, for example, for the SecHCI passwords of your banking cards, you are strongly suggested setting and changing them in the reception desks of your banks, not at your home, your office or any public space.
Tips:
1. How to determine the values of Password Length (K) and Challenge
Length (L)?
The two values are determined by the balance of the desired security
and usability you want in practice. 1) Security: The complexity
of exhaustive attack is C(N, K)=C(KL/3,
K), for default values (K=14, L=30),
it is about 262.5 (the security of a 8-character textual password).
Thus, the larger C(KL/3, K) is, the
better security will be. 2) Usability: The larger L
is, the more challenge-pictures will be displayed in a web page, the more
slowly you make right responses, and you will commit errors with the larger
probability. The larger K is, the more slowly you set/change
your password, and the more difficult it is for you to remember the password.
Definitely, the smaller K and L are, the better
usability will be. As a natural result, you MUST balance the security
and usability by yourself. We think the default values should be OK for
most applications.
2. How to remember your password with tens (or even more) pictures?
It has been well-known that widely-used fixed textual password is not
secure enough to dictionary attack. In addition, forgetting passwords
is also a very annoying problem in real world. Graphical (or visual) passwords
are developed to relax this problem. Our online SecHCI system also adopts
such an idea. However, it is still rather hard for humans to remember
more than 8 pictures [18-20] and quickly make all responses without errors.
How to solve this problem? We suggest using
a secret Pass-Rule (which is similar to Pass-Algorithm [15]) to
remember your pass-pictures. For example, you can select all flags with
a symbol in their centers as your pass-pictures, and ensure no any flags
with two major colors in your decoy-pictures. Here, your pass-rule is
"flags with center symbols", which is much easiler to
remember for you than those flags (do you think so?). We believe that
everybody can successfully find a good pass-rule that is simple enough
for him but VERY VERY difficult for others (of course, also VERY VERY
difficult for robots to carry out dictionary attack). For more details,
please refer to can be found in Sec. 4.4.2 of [1].
3. What about using local pictures in my computer as pass-pictures?
It is a good idea to enhance the above-mentioned pass-rule. It is obvious
that you can much more easily find a good pass-rule if you can use pictures
in your own computer. In future versions of our online SecHCI system,
we will add this function. To avoid possible attacks, all decoy-pictures
should be selected from local pictues, or SecHCI system MUST automatically
update its picture database (more details will be given in our submission
to USENIX
Security Symposium 2003).
4. What about using CAPTCHAs to enhance SecHCI?
YES! CAPTCHAs are very useful to frustrate robots automatic attacking
online secure services. For our SecHCI system, the identification time
will be too large and unendurable for most humans if cryptographically
strong security to online attacks is required (for 264 attack
complexity, the time may be about ten to twenty minutes!). Obviously,
we can use CAPTCHAs to disabel online attacks. For offline attacks made
by humans, 220 to 230 attack complexity is acceptable
for many applications. There (at least) are two kinds ways to incorporate
CAPTCHA and SecHCI: 1) simply adding an extra CAPTCHA challenge picture
(which can be the background picture of SecHCI web page) in each screen
of SecHCI; 2) using CAPTCHA technology to postprocess each challenge-pictures
shown in SecHCI. The latter is stronger, but requires more computation
load. We will try to add CAPTCHA function to our online SecHCI system.
Free codes and documents: Once our submission is accepted for publication, both the source codes of this online SecHCI system and the electronic draft of the submission will be downloadable in our Online SecHCI system when you successfully log in with your a valid ID. If you would like to use the codes in your system, please keep our copyright claims and approve the following copyright claims.
Copyright Claims:
SecHCI is a free ASP web service; you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by the
Free Software Foundation; either version 2 of the License, or (at your
option) any later version. This program is distributed in the hope that
it will be useful, but WITHOUT ANY WARRANTY; without even the implied
warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details. You can see a copy of the
GNU General Public License by click here;
if not, write to the Free Software Foundation, Inc., 59 Temple Place,
Suite 330, Boston, MA 02111-1307 USA
All icons used in our system are randomly collected from Internet, and their authors hold the copyrights. If you (author of some used icons) think I violated your rights, please inform me via e-mail (hooklee@hooklee.com or hooklee@mail.com) and I will immediately stop using your icons.
This site is maintained by Shujun
Li, last updated on 13 August, 2011.